
25
يونيوCybersecurity as an Essential Element of Modern Asset Security Methods
 In today's electronic age, shielding assets expands beyond physical and economic safeguards to include robust cybersecurity steps. Cyber dangers such as data violations, ransomware assaults, and identity theft position significant dangers to people, services, and companies. Applying reliable cybersecurity approaches is vital for securing digital properties, protecting reputation, and keeping functional continuity.
In today's electronic age, shielding assets expands beyond physical and economic safeguards to include robust cybersecurity steps. Cyber dangers such as data violations, ransomware assaults, and identity theft position significant dangers to people, services, and companies. Applying reliable cybersecurity approaches is vital for securing digital properties, protecting reputation, and keeping functional continuity.
Relevance of Cybersecurity for Property Defense
Cybersecurity plays an important duty in property medicaid asset protection trust by securing digital properties, sensitive details, and copyright from malicious actors and cyber threats. Personal and monetary information, profession secrets, proprietary modern technologies, and consumer information are valuable properties that require detailed protection versus unauthorized gain access to, burglary, and exploitation.
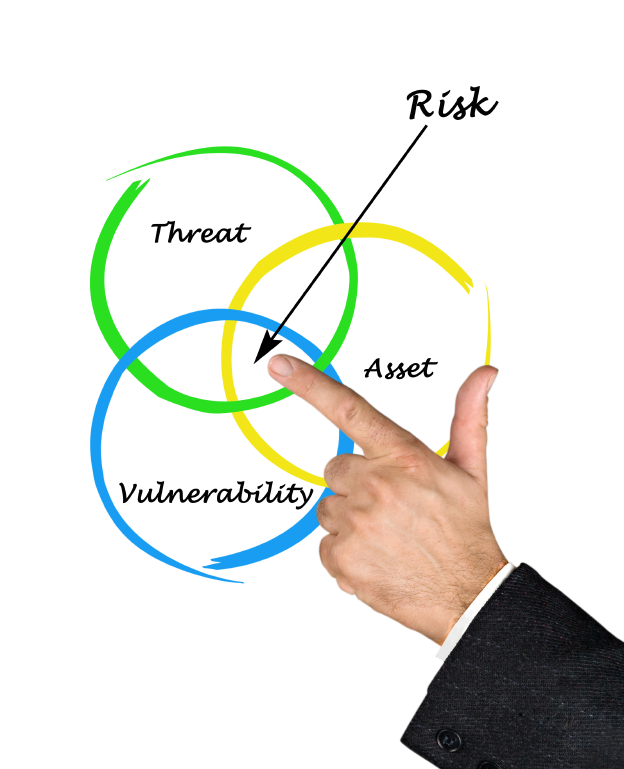
Danger Analysis and Susceptability Administration
Performing routine danger analyses and susceptability scans aids recognize possible cybersecurity dangers and weak points within systems, networks, and applications. By assessing vulnerabilities and applying prompt mitigation procedures such as software updates, spots, and safety setups, people and companies can proactively decrease direct exposure to cyber hazards and strengthen total property security.
Data Security and Accessibility Controls
Securing delicate information and implementing durable gain access to controls are essential cybersecurity methods for protecting digital properties. File encryption converts data right into unreadable layouts that can only be decrypted with certified gain access to qualifications or keys, ensuring confidentiality and stability. Access controls restriction customer permissions based upon roles and obligations, stopping unapproved individuals from accessing sensitive info and essential systems.
Event Action and Service Connection Preparation
Creating and applying incident response plans and company connection techniques are important for minimizing the influence of cyber cases on asset protection trust security. Quick detection, containment, and recuperation procedures allow speedy feedback to cyber assaults, lessening functional disruptions and monetary losses. Organization continuity planning ensures that vital features and solutions can continue continuous in the event of a cyber incident or data breach.
Employee Training and Understanding
Enlightening workers concerning cybersecurity best practices and raising recognition regarding emerging risks are crucial elements of reliable living trust asset protection protection strategies. Educating programs on phishing understanding, password hygiene, secure surfing behaviors, and social engineering methods empower employees to recognize and report suspicious activities, minimizing the danger of human error and insider hazards.
Conformity with Rules and Criteria
Following market laws, legal needs, and cybersecurity standards is imperative for preserving conformity and boosting property defense. Laws such as GDPR (General Information Protection Law), HIPAA (Health And Wellness Insurance Mobility and Liability Act), and PCI DSS (Payment Card Sector Information Safety and security Standard) develop guidelines for shielding individual information, health care info, and financial transactions, specifically.
Verdict
Incorporating cybersecurity steps into property protection techniques is crucial for reducing electronic dangers, maintaining confidentiality, and keeping count on in a progressively interconnected globe. By embracing proactive cybersecurity techniques such as threat assessment, information security, access controls, event reaction planning, staff member training, and governing conformity, people and companies can properly protect electronic possessions, alleviate cyber hazards, and guarantee resilience versus progressing safety difficulties.
In today's electronic age, securing assets expands past physical and financial safeguards to include robust cybersecurity steps. Executing efficient cybersecurity strategies is important for guarding electronic possessions, maintaining online reputation, and preserving operational continuity.
Securing sensitive information and implementing durable access controls are essential cybersecurity practices for shielding digital assets. Establishing and carrying out occurrence feedback strategies and organization connection approaches are vital for minimizing the effect of cyber incidents on property defense.



